

Check this one out.
In September, we made you freaks aware of a possible griefing attack against Lightning Network users that was highlighted by developer Joost Jager. The attack is known as a griefing attack because an attacker can only prevent its victim from moving their sats within their channel and causing them to pay a very large fee from having to close a channel with a lot of UTXOs. In a worst case scenario, an attacker could attempt to ransom a user's channel and ask for payment to stop the attack. However, there's no way to know whether or not they will actually stop the attack.
Here's a great piece from Jestopher that was published on Bitcoin Magazine yesterday. The piece details an experiment Jestopher ran with Joost, Clark Burkhardt and Phillip Sheppard in which Joost played an attacker and Jestopher, Clark and Phillip played victim nodes. This was all conducted on the Lightning Network's mainnet and executed successfully.
This is a great way to learn more about the nature of this particular griefing attack, how attackers can easily take advantage of the inherent 483 HTLC limit in the protocol, how to know if you are being attacked, and potential solutions to solve this particular attack vector.
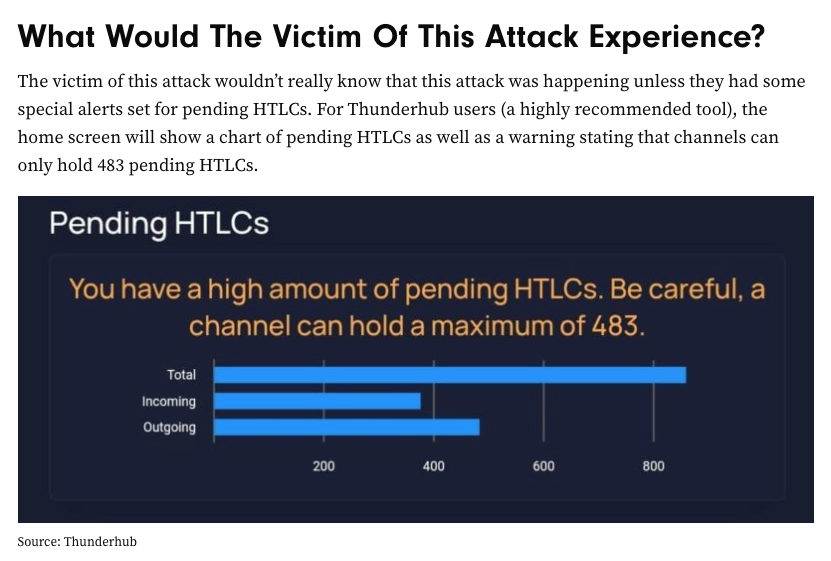
At the moment, it seems that the only tool one can use to easily track their incoming and outgoing HTLCs is Thunderhub. This isn't ideal, but, as I said when I initially posted about Joost talking about this attack vector, the fact that individuals are probing around this particular problem and highlighting where pain points exist in terms of being able to recognize you are being attacked, thwarting it while it's in progress, or completely mitigating it in the first place. Shoutout to Jestopher, Joost, Clark and Phillip for adding valuable data points to these research efforts.
If you are able to help Joost and others as they build out their circuitbreaker solution to this problem, please reach out to them!
Final thought...
Crew neck and dad hat type of Tuesday.