

This is not ideal. It's probably not a good idea to create bitcoin private keys with Apple M-Series chips.
A team of academic researchers has disclosed a significant vulnerability in Apple's M-series chips that could allow attackers to extract secret cryptographic keys, as detailed in a recent paper published on Thursday. This hardware-based flaw, arising from the microarchitectural design of Apple's silicon, is particularly concerning because it cannot be easily patched; instead, it necessitates the incorporation of defenses into cryptographic software, which may severely impact performance, especially on earlier M1 and M2 chip generations.
The vulnerability exploits a side channel in the chips' data memory-dependent prefetcher (DMP), a feature intended to reduce latency by predicting and preloading data into the CPU cache. However, this optimization has inadvertently opened a pathway for attackers to leak information through memory access patterns, challenging the effectiveness of constant-time programming—a technique used to protect cryptographic operations from similar attacks.
Researchers Boru Chen, Yingchen Wang, Pradyumna Shome, Christopher W. Fletcher, David Kohlbrenner, Riccardo Paccagnella, and Daniel Genkin have named the attack 'GoFetch.' They explain that the DMP differs from traditional prefetchers by sometimes misinterpreting memory content as an address and prefetching data based on those values, thereby leaking sensitive information through the cache.
The GoFetch attack can be executed by an application with normal user system privileges, requiring no root access. It is effective against both classical encryption algorithms and those designed to be quantum-resistant. The researchers demonstrated the capability to extract various cryptographic keys, including a 2048-bit RSA key within an hour and a 2048-bit Diffie-Hellman key in just over two hours.
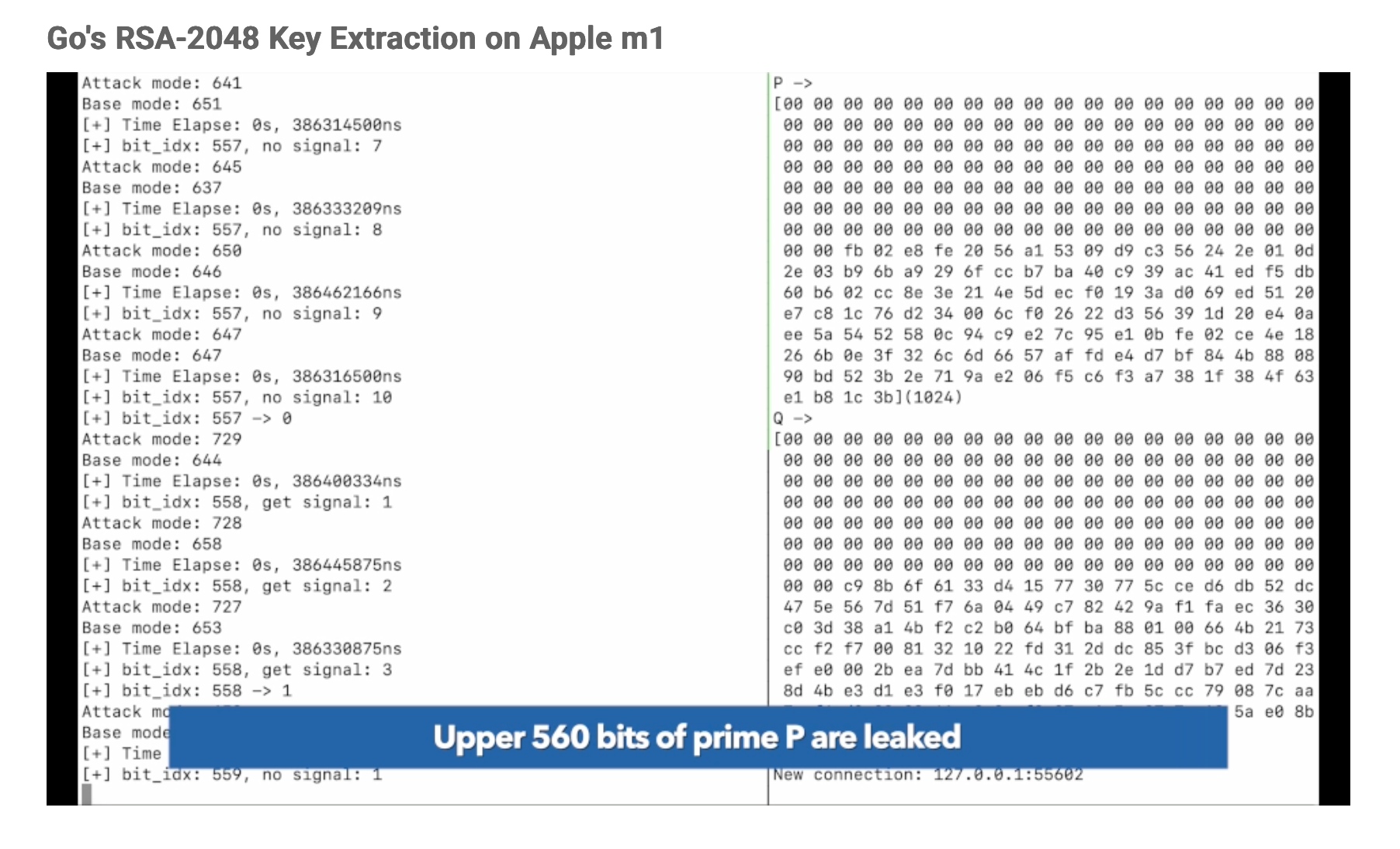
Mitigating this vulnerability presents a significant challenge. One potential defense is ciphertext blinding, which can be costly in terms of computational resources. Another is to offload cryptographic processes to efficiency cores within the chip that do not have DMP, although this could slow down operations. The latest M3 chip includes a feature allowing developers to disable the DMP, but the performance impact of this measure is not yet clear.
Apple has not commented on the record regarding the GoFetch research. Users concerned about the security of their Macs should look out for updates on GoFetch mitigation measures for macOS software implementing the affected encryption protocols. The researchers caution that manual cryptanalysis and code inspection are necessary to determine vulnerability, suggesting that other cryptographic protocols could also be at risk.
The discovery of this vulnerability underscores the ongoing battle between hardware performance optimization and security. As the industry continues to grapple with the implications of this research, developers and end-users alike must remain vigilant in updating and securing their systems.
Originally reported in Arstechnica